I've been written Basic Fortigate Unit Configuration up to part 1 to 6.
Now...I am going to write Advance Configuration Steps.
Most of the Company have two Internet Line for Primary and Backup.
I'd like to write how to setup two Internet line on one Fortigate unit.
Let's assume Primary Internet Line use Static IP and Backup Internet Line DHCP IP.
Here, I will use some IP address to configure Fortigate. You need to use real IP address of yours instead.
Firstly, I'm gonna setup Primary Intenet line.
- Connect the Line from Primary ISP to the WAN1 Port of Fortigate Unit.
- Log in to Fortigate by using Web-based Manager.
- Go to System>Network>Interface and Select WAN1 Interface. Then Edit as following picture
- Select Internal Interface and Edit as following,
- Go to Router>Static>Static Route and Select Create New. Add Default Route then.

- Go to System>Network>DNS. Add Primary, Secondary DNS serers address.
- Go to Policy>Poliicy>Policy. Select Create New and define the Security Policy as following picture to get Internet Access for Private/Internal Network through from WAN1 interface.
Some Fortigate Model configured this as Default Policy.
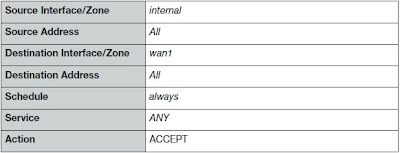
- Select Enable NAT and Use Destination Interface Address.
- Select OK to save Security Poliicy.
Primary Internet Line Setup Task done. Now I'm gonna setup Backup Internet line.
- Connect Backup Internet Line to WAN2 port of Fortigate.
- Log in to Fortigate by using Web-Based Manager.
- Go to System>Network>Interface and Edit WAN2 Interface.
- Change Addressing Mode to DHCP. Select Retrieve Default Gateway from server. Uncheck the Override internal DNS checkbox.
- Select OK to save.
(Do not forget to select Retrieve Default Gateway from server to add Default Route into Routing Table)
- Go to Policy>Policy>Policy. Select Create New and Define Security Policy as following picture. To get Internet access from Private/Internal Network through from WAN2 interface.
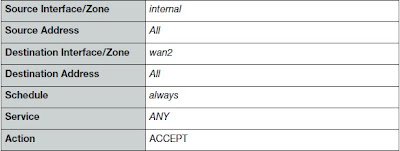
- Select Enable NAT and Use Destination Interface Address.
- Select OK to save Security Policy.
Backup line setup done.
Now I'm going to set the default route to WAN1 to be the primary default route and add a ping server for WAN1 and WAN2
The Ping Servers Verifiy the ability of the WAN1 and WAN2 interfaces to connect to the Internet.
- Go to Router>Static>Static Route. Edit the WAN1 Default Route. Select Advance and set Distance to value to 10. (By Default it is 10).
- Go to System>Network>Interface. Edit the WAN2 Interface. Set Distance to value to 20. ( The value of Distance to can set any number higher than 10)
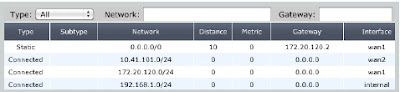
- To confirm which default route is now actually being used by the Fortigate unit, go to Router>Monitor>Routing Monitor to view the current Fortigate routing table.
- Go to Router>Static>Settings. Select Create New and Add Ping Server for WAN1 as following picture,
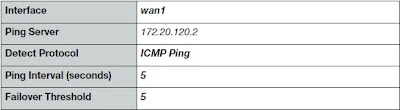
- Add Ping Server for WAN2 as following picture.

OK... Now settiing up two Internet line in one Fortigate unit is done.
May you all be happy.
(Be knowledgeable, pass it on then)



Comments
Post a Comment